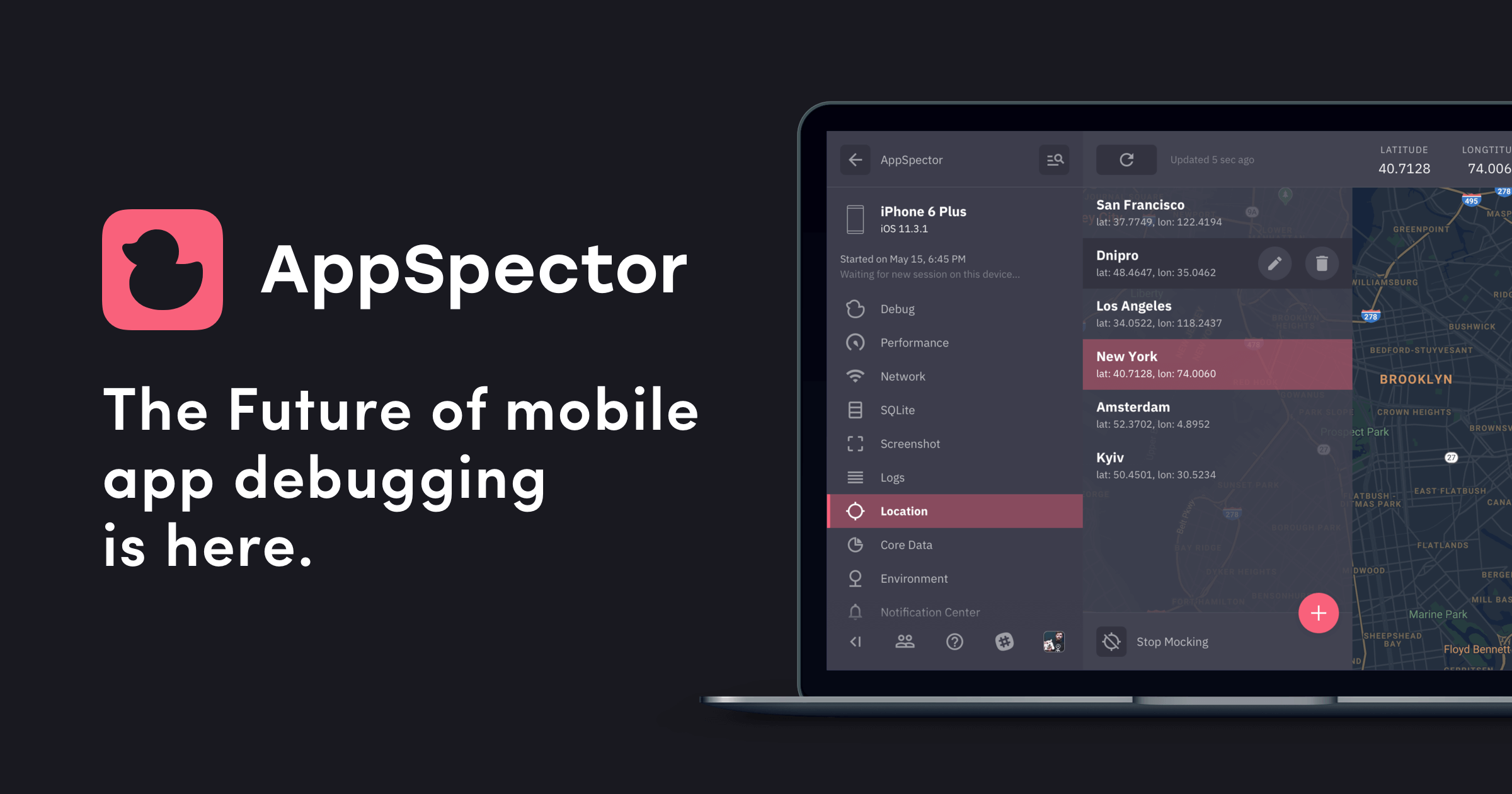
End-to-end encryption (E2EE)solutions
Many names, one concept. End-to-end encryption, Zero-knowledge protocols and architectures, zero-trust access control and security solutions all address one thing: building systems with elevated security requirements, where only trusted agents are allowed to access the data.
The challenge of E2EE / Zero Trust solutions is the combination of security, maintainability and flexibility, which doesn't ruin UX.
Challenges that require E2EE solutions
Hard to control
Huge heterogeneous infrastructures with tons of components and weak perimeter in "we can't be sure what's trusted" state.
Elevated risks
Compliance requirements or real-world risks that require minimisation of attack surface and maximisation of protection and visibility.
Insider threats
E2EE and Zero Trust systems have defenses "outside" and "inside", protecting data from curious employees, leaving no opportunities for insiders.
Modern end-to-end encryption solutions
Modern crypto protocols
Zero-knowledge proof protocols allow parties to process the data together without revealing it to each other or 3rd parties. This minimises the exchange of plaintext data inside the system.
Zero Knowledge Architectures
ZKA is a design principle that facilitates building products with no access to customer data, be it directly or via inference. ZKA can be built on top of end-to-end encryption.
Zero Trust access control
Systems that don't have a "trust perimeter". All components are required to verify access on every transaction based on the security-relevant context of this transaction.
Our offerings
// End-to-end encryption software
Acra
A DATABASE SECURITY SUITE
Themis
A CROSS PLATFORM CRYPTO LIBRARY
// Custom design and implementation
Zero Trust and Zero Knowledge systems
End-to-End Encryption layers
Differential privacy systems
// Consulting
Designing architecture for your use case
Reviewing application security
Product security strategy
Have a question? Get a human to answer it!
Business impact
User trust
Your company doesn't have access to users' data. At the same time, the end-to-end encryption layer is integrated into app flow without breaking UX.
Decreased cognitive load
Zero Trust, Zero Knowledge systems are hard to build, maintain and control. Our experience allows making them developers and Ops friendly.
Simpler compliance
Controlled data flows inside strict security tools is easier to validate with auditors. Plaintext data can't be unnoticeable leaked if it's almost never in plaintext.
Reduced risk
Zero Trust, Zero Knowledge systems radically decrease the attack surface for data and access and improve visibility.
For innovators, by innovators
We've started Cossack Labs to develop new tools and methods for protecting the data and enabling novel solutions to emerging problems — so that at the edge of your innovation, you’ve already got fitting tools handy.
Contact us
There are many ways we can help: with our products, bespoke solutions, and engineering services. Leave your contact information to connect with our team:
Relevant blogposts

PII Encryption Requirements. Cheatsheet
What data is sensitive and needs to be encrypted according to data privacy regulations like CCPA, GDPR, HIPAA, etc.? Our cheatsheet addresses this question

Implementing End-to-End encryption in Bear App
Helping Bear app implement note encryption for their vast existing user base. Balancing usability, security, and mobile platforms' restrictions.
Zero Knowledge Protocols without magic
Zero Knowledge protocols are often used for authentication, as they allow two parties to verify whether they share the same secret without revealing it. We explain different use cases and how to use them on practice.