Cybersecurity,tailored for your mission
We solve security challenges in complex mission-critical systems end-to-end: we deliver R&D, services, developer tools and bespoke solutions addressing practical risks in high-stakes scenarios.
Enhancing Ukraine’s cyber resilience
Cossack Labs stands with Ukraine. We bring our diverse range of capabilities to all needing forces, organisations and agencies that help protect Ukraine across critical infrastructure, defence and government.
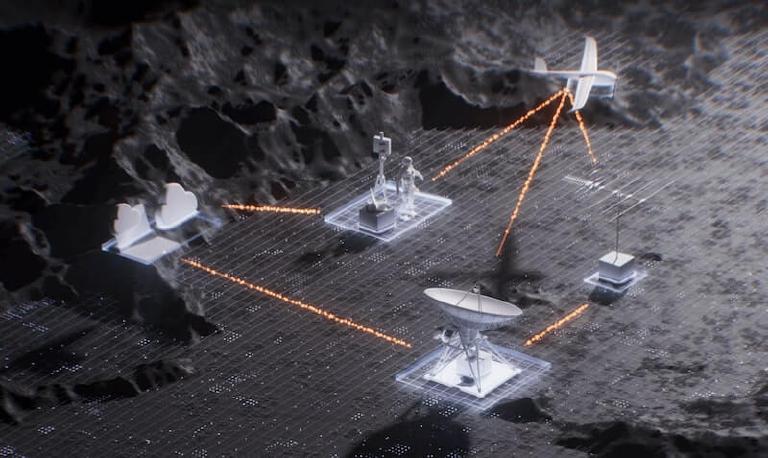
We operate where the risks are #
We bring tailored security solutions to innovators operating in the world’s most demanding environments.
Defence
Energy
Finance
Consumer Apps
Healthcare
IoT, Robotics and Hardware
What our customers say
About Cossack Labs
We are on a mission to make the world a safer place for everyone in the future. We work with those who build tomorrow’s technology to protect the people who rely on it. We are allies with those who look at technological progress through these lenses of responsibility, careful engineering, well-thought decisions that build a safer future.
Contact us
There are many ways we can help: from R&D to professional services, from open-source developer tools to bespoke solutions. Leave your contact information to connect with our team:
Latest blogposts

How mobile app analytics library led to the PII exposure
Vulnerabilities in third-party libraries: Exploring a real-world case where an update in an analytics library exposed personal data. We’ll cover the entire journey from discovering the i...

SBOM from the security perspective
Despite being a potential approach for enhancing software supply chain security, SBOM’s own flaws and complexities in implementation may be holding back its goal to improve software tran...
Protecting ML models running on edge devices and mobile apps
Machine Learning models are a significant investment in competitive advantage; thus, companies are willing to walk the extra mile to protect them. ML model security is even more critical...