Building security for M&A solutions: 5-years of SSDLC
Long-term cooperation with the [REDACTED] company resulted in refined security practices that matched the evolution of their B2B platform.
We enabled transition from reactive "firefighting" to a proactive security posture, while simplifying security processes and building security defences.
Overview
Our client, a global leader in secure Virtual Data Rooms for Mergers and Acquisitions (M&A), empowers businesses to safely navigate sensitive information exchange during deals. Their SaaS platform ensures secure cooperation and document sharing between the parties, offering granular access control, advanced analytics, comprehensive project management tools, and additional services to support the deal lifecycle.
During our multi-year cooperation, we improved product security by addressing security at each development phase and adopting robust security mechanisms to mitigate potential risks and prevent security incidents. We established proactive security processes, having streamlined and documented practices for enhanced clarity, stability, and logical flow.
Industry
M&A SaaS provider
VDR
Diligence and productivity software
Technology stack
iOS, Android native apps
React Native mobile apps
GraphQL, REST and Java backend
Regulations
CCPA, GDPR, HIPAA
Internal security policies
Encryption Export Regulations
Challenges
Proactive security posture management
Having recognised the limitations of annual pentests, the client realised the need for a dedicated application security team able to design and build product security together with their product team.
Security development processes should be easy to follow
The need for well-documented security processes to ensure consistent application and efficient knowledge transfer. The security processes are to be simple, logical, nicely described and stable so that new engineers could nicely adopt them.
Shifting mobile applications from native to React Native
Security should be suitable for the new technological stack. The development team should adapt security strategies to the specifics of React Native, as well as incorporate additional robust security measures, tailored to the nuances of cross-platform framework.
Technology requirements
Long-term mitigation strategy
The mobile application requires appropriate security controls and issues mitigation, considering iOS, Android and React Native threats. Adaptability and maintainability are crucial to avoid security regressions.
Flexible security architecture
Scaling and evolving security architecture, capable to meet their objectives and keep pace with the company’s development. The product is being continuously upgraded to meet the organisation's growth.
Security tailored to product goals
Leveraging client feedback to prioritise and adjust security controls, equip teams for seamless integration with the client’s standards to meet their expectations.
Our approach
Tailored SSDLC process:
Applying security best practices to each development phase: security architecture review, designing and building complex security controls, secure code review of implemented changes, security testing, regression testing, creating scripts for CI/CD pipeline to automate security validation, security review of production configuration, and many more.
Measurable security:
We are using a security verification standard—an extended, supplemented and project-tailored version of OWASP MASVS—to measure product security posture and calculate a “security score”. It makes security tangible and comparable, tracking how new features and other changes impact project security.
Continuous monitoring of new threats and risks:
Our team keeps the developers informed about the latest state-of-the-art security controls. We keep monitoring for the newest vulnerabilities and CVEs relevant to the platform, ensuring that the product team is always equipped with the most current and effective security measures.
Solution
Application security expertise
- Reverse engineering protection for mobile apps: In collaboration with the client’s team we built a strong anti-tamper system, seamlessly integrated with the client's business needs. The system functions natively on both iOS and Android, using relevant platform-specific features.
- Data protection and cryptography: The mobile application stores and processes sensitive data, including user credentials. We developed a multilayer data encryption scheme for local storage, integrated with hardware encryption modules (SecureEnclave, hardware-backed KeyStore).
- Resilience and defense-in-depth solutions: Having successfully implemented basic security controls, we moved to the defense-in-depth level, offering more complicated security controls to mitigate specialised threats and cover a wider attack surface.
Providing security guidance on complex features
- Adapting Security for React Native Transition: Helping the client to 'transfer' their main security features and controls from the native platforms for functionalities that couldn't be transferred directly. We provided hands-on support to rebuild them from scratch within React Native, ensuring no downgrades in security.
- MDM adoption: We guided our client through the entire process of distributing a special application’s flavour via Mobile Device Management (MDM) system from idea to implementation. During the design and architecture stage, we articulated certain security focus points. We also assisted the implementation process and performed security verification after each significant change of the source code.
- Navigating the compliance landscape of data sharing: We were supporting the development team in adhering to laws and regulations, applicable to the product. Assessing cryptographic practices relevant to the encryption regulations, and advising on secure data exchange through informed legal involvement.
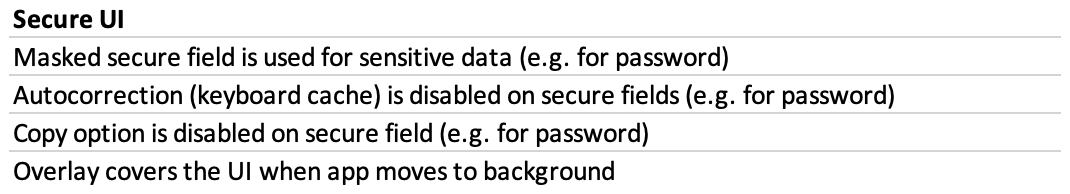
An example of one of the sections in security regression checklist that is completed in for each release
Security processes
- From basic controls to advanced security: Our successful five-year journey resulted in evolving from the basic security standards to the Cossack Labs Mobile Security Score (CL MSS). CL MSS is an extended and project-specific requirements standard designed to maintain security posture stability while meeting increasingly complicated demands. It has 160+ requirements and focuses on security controls relevant to the project. Following this standard, we have identified 30 more issues and improved resilience, data and network security aspects of the apps.
- Documenting security controls and decision-making results: We log a history of made decisions for implementing or not implementing particular security controls. It allows accepting potential risks while demonstrating that the absence of particular features is not a bug, but rather a conscious security decision. These decisions are reviewed and discussed on a regular basis, as well as demonstrated to the company's customers as the genuine and relevant aspects of the security posture.
- Providing mobile security expertise in incident response: In case of an ongoing security incident our team switched to an emergency mode. Our security team is ready to assist the development in investigation, prioritisation, mitigation and fix verification in a timely manner. There was only one incident in the last couple of years, proving the stability of implemented security controls.
- Immediate support and on-demand results: Sometimes security controls cause false positive reactions, preventing legitimate users from fully using the application. One example is that iOS reverse engineering protection was accidentally activated on a specific iPhone after the app detected potential malware due to a software conflict. Such situations required our immediate attention to debugging, recognising, and enhancing reverse engineering detection. As mobile operating systems evolve fast, such cases arise on occasion.
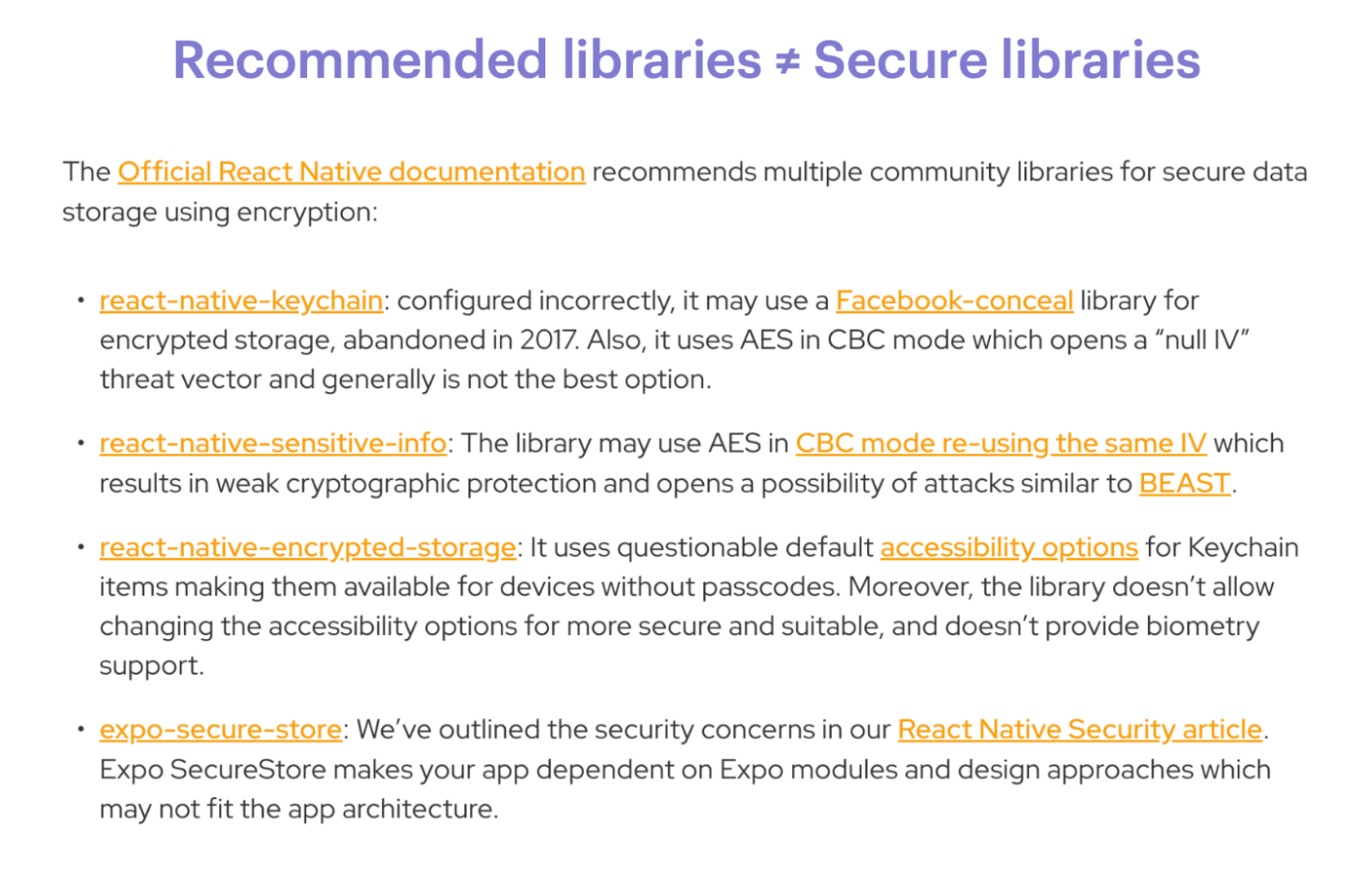
A screenshot from our lecture about dependency management recommendations for React Native libraries.
Assistance in dependencies management process
- Third-party libraries evaluation: When developers want to add new open source libraries or components to their app they discuss it with us, their security team, especially when the library has a potential security impact. We perform a rapid security assessment to see if the library is well-supported, checking it for existing vulnerabilities or issues. We also briefly read the code to give the green light to use it or to point to issues why not. Once the library is integrated, it becomes a target for the ongoing automated dependency and vulnerability management checks.
- We established a regular dependencies update process with developers. Before updating libraries with sensitive functionality, the dev team assesses whether new versions introduce vulnerabilities to the product. After an updated build is completed, we conduct additional security verifications to ensure security integrity.
- Vendor evaluation: We check and analyse 3rd party SaaS services (analytics, crash reporting, dev tools, etc.), examine their mobile SDK and comment on the things that don't look good from a privacy & security perspective. We explain which security services should be included if the client decides to use this option. Thus we have a special track on working with vendors, especially if they have security issues.
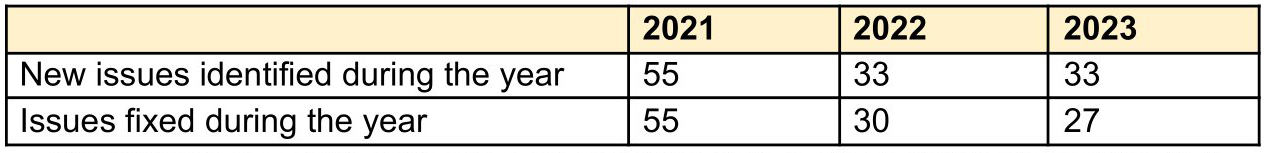
The number of security issues in open and done state for the last 3 years showing that security evolves together with the product functionality
Collaborating as an internal security team
- Developer-centric weaknesses and vulnerability reports: We offered new security controls and improvements to enhance communication and remediation of complex issues for developers. From now on they can see what needs to be done and the impact. The issues are to be described in a clear and understandable manner/language, the step-by-step guidance is required during the whole process.
- Fostering security onboarding: We provide the new team members with clear security controls, backed with comprehensive documentation, training, and workshops. This practice enhances their security awareness and builds their mobile platform-specific technical skills.
- Maintaining strong communication with the client’s internal security team. Thus if they have any questions related to the mobile security and the surrounding environment it is operating in, we are ready to help. This cooperation with the internal security team enables us to communicate our concerns on the general infrastructure where mobile apps operate. It also allows seeing the big picture, and ensures that security controls—integrated in different parts of the system–are synchronised and optimised.
Products and services involved
Themis, a cross-platform crypto library
Themis is a cross-platform high-level open-source cryptographic library. We used Themis as a building block for cryptographic protocol, focusing on the data flow and performance while having cryptography covered.
Read moreThemis, a cross-platform crypto libraryMobile app security
We've designed & implemented numerous platform-specific security controls for mobile apps, including reverse-engineering protections and mobile device attestation, and the cryptographic layer for sensitive data protection.
Read moreMobile app securitySecurity advisory
We've built risk, threat and trust models, analysed and prioritised attack vectors, planned security controls and assisted with implementation and verification of controls.
Read moreSecurity advisorySecurity engineering
We've recommended improvements in backend API security and aligned security measures across platforms.
Read moreSecurity engineering
Results and outcomes
Shifted security efforts from firefighting to proactive work
We managed to make security a seamless part of the workflow, fostering clear communication between product and development teams. We enabled transition from reactive "firefighting" to a proactive security posture, while simplifying security processes and making them well-documented, simple, stable, and logical.
Making security less frustrating for the product team
We led and maintained SSDLC and security processes the [REDACTED] company didn’t have at the very beginning of our cooperation. By regularly providing knowledge base and expert assistance for development and QA teams, we enhanced cooperation within the teams. We tailored security to product goals and clients’ expectations, maintained flexible security architecture and enhanced security posture of our client’s platform.
Stable 80% security score for 2 years
Stable security score and not growing backlog are the achievements of our long and fruitful cooperation with the client. Measurable results and the ability to track them through the years helps in defining the security roadmap of the product and enhance security even further. As a result, no issues were found during recent external penetration testing, making our client satisfied with our cooperation.
Client satisfaction via enhanced security
From now on our client’s platform has all the security controls that their customers typically require. So when our client receive security questionnaires and RFIs, they can provide clear and thorough answers promptly. Thus our client gets satisfied customers and we get a satisfied client.
Contributing to evidence-based reputation on the market
As of today, our client has a well-educated team, timely and effectively managing all security processes. Stable strong security posture, proactive security approach, little-to-no emergency situations, smooth and well-managed security processes make our client and their software platform attractive on the market.
Breaking is easy, building is hard
We work together with your engineers to not only identify security weaknesses, but also to build effective defences that align with your product's security posture and your team's level of engineering expertise.
